In a staggering breach rattling the cryptocurrency world, Bybit, one of the world’s leading crypto exchanges, fell victim to a $1.5 billion Ethereum theft. The largest heist in crypto history! The hack, executed during a routine wallet transfer, once again calls into question the security of centralized exchanges. While Bybit has acted swiftly to replenish user funds and restore services, the incident has reignited debates over the vulnerabilities of centralized platforms. Is the industry prepared to counter increasingly sophisticated cyber threats?
How the Bybit Hack Unfolded
The breach occurred on February 21, 2025, during a scheduled transfer from Bybit’s cold wallet to a warm wallet. According to blockchain forensic analysis, attackers exploited weaknesses in the wallet management process. They bypassed multi-signature safeguards through either compromised credentials or advanced phishing tactics. Bybit detected the unauthorized transfer within minutes, but due to the decentralization and irreversibility of blockchain transactions, it could not halt the siphoning of approximately 395,000 ETH (valued at around $1.5 billion at the time). Following the breach, the attackers moved the stolen funds through multiple wallets and laundered them via decentralized exchanges (DEXs), cross-chain bridges, and privacy-focused mixing services, including Tornado Cash. These laundering methods complicated recovery efforts despite ongoing blockchain analysis and law enforcement collaboration.
Who Is Behind the Attack?
While the investigation is ongoing, preliminary reports from cybersecurity firms and blockchain analytics companies point toward the North Korean state-sponsored hacking group Lazarus, well known for targeting cryptocurrency platforms to fund the regime’s activities. No definitive attribution has been made, but the tactics employed mirror previous attacks linked to Lazarus, including the use of mixing services and decentralized exchanges to launder stolen funds.
>>> Read more: Crypto Hacks 2024: Lessons from $2.2 Billion in Losses
Bybit’s Response and Recovery Measures
In the wake of the breach, Bybit CEO Ben Zhou addressed the incident publicly. He reassured users that “all customer assets remain secure and fully backed 1:1.” The exchange acted swiftly, replenishing $1.23 billion worth of stolen Ethereum through a combination of market purchases, whale deposits, and emergency loans. To incentivize the recovery of the stolen assets, Bybit announced a $140 million bounty for information leading to the recovery of funds.
Operationally, Bybit paused certain wallet functions and, as of February 24, 2025, is working to fully resume those services. The exchange has emphasized implementing enhanced security measures and plans to release an audited proof-of-reserves report in the coming weeks.
Impact on the Cryptocurrency Market
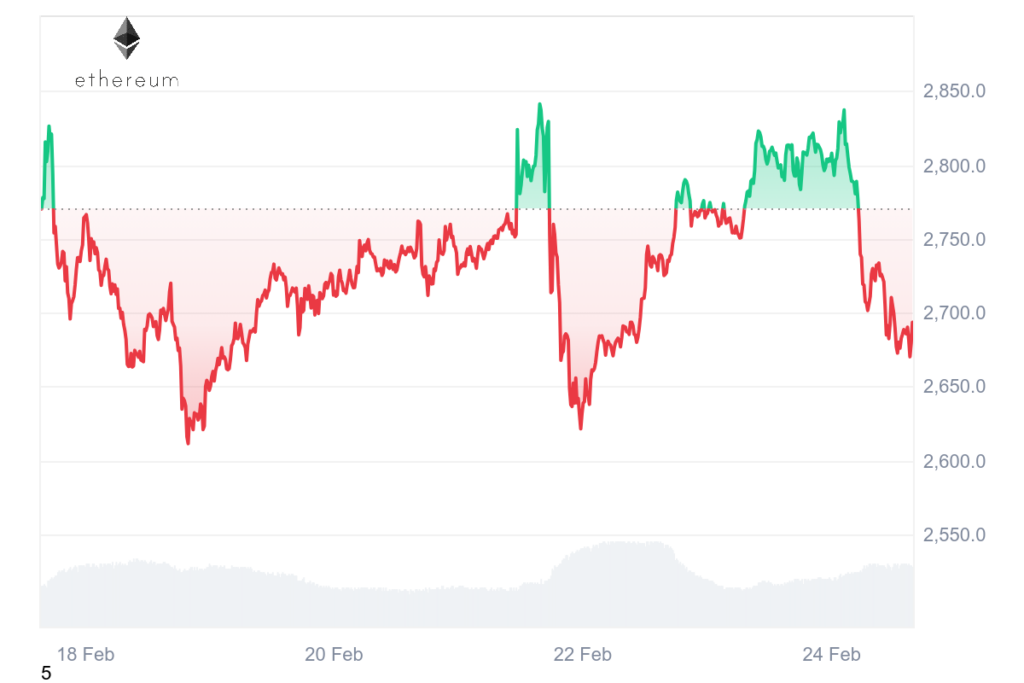
The immediate aftermath of the Bybit hack triggered a market-wide reaction. Ethereum prices dropped nearly 7% as news of the theft spread. Bitcoin and other major cryptocurrencies also experienced declines, reflecting shaken investor confidence in centralized exchanges. Analysts note that such incidents underscore the importance of robust custodial solutions. It may accelerate the adoption of decentralized exchanges (DEXs), where user-held keys offer enhanced security.
Industry Implications and Security Concerns
The Bybit breach highlights the persistent vulnerabilities faced by centralized cryptocurrency platforms. Despite advancements in cybersecurity, exchanges remain prime targets for cybercriminals, especially during wallet transfers and system upgrades. Experts emphasize the need for multi-layered security strategies, including hardware wallet integration, decentralized custody solutions, and rigorous internal access controls.
Regulatory scrutiny is also expected to intensify following the incident. Authorities in Asia and Europe have already called for heightened oversight of exchange security standards, potentially leading to new compliance requirements around wallet management and user fund protection.
>>> Read more: North Korea Crypto Hackers Undermine the Crypto Ecosystem
While Bybit’s swift response has been lauded in some circles, the incident is a stark reminder of the risks associated with centralized platforms. For investors, the breach reinforces the importance of self-custody and due diligence when selecting trading venues. For the industry, it marks a pivotal moment to reassess and fortify security protocols amid escalating cyber threats.
As investigations continue and the crypto community watches closely, the Bybit hack will undoubtedly shape discussions around digital asset security and the future of centralized exchange infrastructure.
Readers’ frequently asked questions
How can hackers steal cryptocurrencies during wallet transfers, and why could Bybit not stop the theft immediately?
Hackers exploit vulnerabilities in the transfer process between wallets, especially when moving funds from a cold wallet (offline storage) to a warm wallet (semi-online storage). In Bybit’s case, the attackers bypassed the security protocols during this scheduled transfer. Despite having detection systems in place, cryptocurrency transactions on the blockchain are irreversible once confirmed. So, even though Bybit noticed the unauthorized transfer within minutes, it could not reverse the transactions or stop the funds from being moved once they were validated on the blockchain network.
What happens to the stolen cryptocurrencies after a hack like this, and how do authorities try to recover them?
After a hack, attackers often use tactics to obscure the movement of stolen funds. They transfer the cryptocurrency through multiple wallets and use cross-chain bridges to switch between blockchains. They also rely on mixing services like Tornado Cash to, ultimately, break the traceable link between transactions. Authorities and blockchain analytics firms track these movements using specialized software. They identify wallet patterns and potential exchange points where stolen assets might be converted to fiat currency. Recovery is challenging and slow, but sometimes funds can be frozen if hackers attempt to cash out on regulated platforms.
How can users protect their cryptocurrency assets and avoid risks like those seen in the Bybit hack?
Users can protect themselves by practicing self-custody. They should store their cryptocurrencies in personal wallets, particularly hardware wallets, instead of keeping them on exchanges. Using wallets that require multi-signature approvals or two-factor authentication adds additional security. It’s also crucial to avoid sharing sensitive information online and to use reputable, regulated platforms when trading and holding assets. While large exchanges like Bybit offer convenience, they also present single points of failure. Diversifying storage solutions and staying informed about security best practices can significantly reduce risk.
What Is In It For You? Action Items You Might Want to Consider
Prioritize Self-Custody for Your Assets
Relying solely on centralized exchanges exposes you to risks beyond your control, as the Bybit hack illustrates. Consider transferring the majority of your holdings to secure cold wallets. Hardware wallets and self-custody solutions offer greater protection against exchange breaches. Don’t wait for another incident. Take control of your assets today.
Diversify Trading Platforms and Stay Informed
Even top-tier exchanges aren’t immune to cyberattacks. Spread your trading activities across multiple platforms to mitigate potential losses in the event of a breach. Subscribe to trusted security alerts and industry news to stay updated on platform vulnerabilities and evolving cyber threats. Knowledge is your best defense.
Use Stop-Loss Orders and Monitor Market Reactions
Hacks of this scale can trigger significant market volatility. Be proactive and set stop-loss orders to protect your portfolio from sudden downturns, like the 7% dip in Ethereum following the Bybit incident. Pay close attention to market reactions after security events; sometimes, volatility presents lucrative short-term trading opportunities if approached with caution.









[…] the Lazarus Group executed a staggering $1.5 billion heist on cryptocurrency exchange Bybit, it sent shockwaves throughout the digital asset world. The North Korean-backed hackers exploited […]
[…] were exploited to facilitate money laundering operations. This follows an extensive probe into the Bybit hack. In what has been described as one of the largest cyber breaches in the industry the exchange saw […]