As the cryptocurrency market continues to mature, so do the threats it faces. In 2024, hackers exploited vulnerabilities across the blockchain ecosystem, resulting in a staggering $2.2 billion loss – a 21% increase from the previous year. This sharp rise underscores the increasing sophistication of cybercriminals and the challenges faced by the industry in safeguarding digital assets. While December recorded the lowest monthly losses this year, with $29 million lost, the overall trend paints a grim picture of an industry struggling to keep pace with evolving threats.
The Shift in Targets: Centralized Exchanges Under Fire
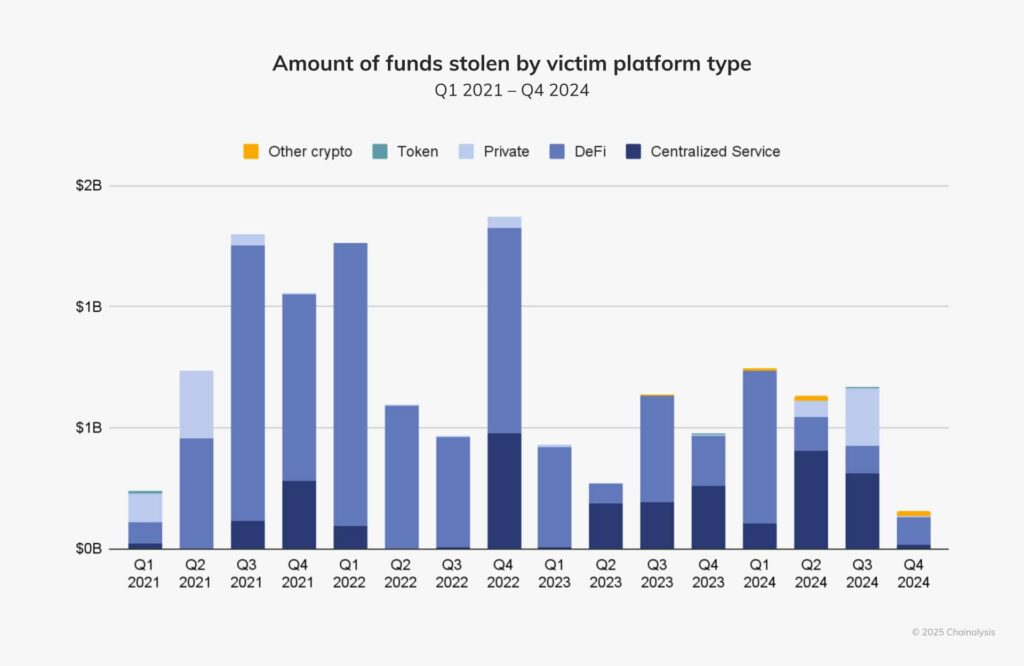
Traditionally, decentralized finance (DeFi) platforms bore the brunt of cyberattacks due to their reliance on vulnerable smart contracts. However, 2024 saw a marked shift in hacker focus toward centralized exchanges. These platforms, which hold large concentrations of user funds, became lucrative targets for cybercriminals. Notable incidents include the $305 million breach of DMM Bitcoin in May and the $235 million heist from India’s WazirX in July. These breaches highlight significant security lapses in centralized platforms, particularly around private key management and internal protocols.
Despite their reputation for better security compared to DeFi platforms, centralized exchanges’ weaknesses in safeguarding custodial funds were starkly exposed. This pivot in attack vectors underscores the urgency for centralized platforms to fortify their defenses, adopt advanced monitoring tools, and implement robust security audits.
Additionally, the attacks exposed systemic challenges, including inadequate employee training and a lack of layered security mechanisms. Many of the breaches in 2024 could have been mitigated through stronger access controls, two-factor authentication, and compartmentalized data storage. Centralized platforms now face mounting pressure to restore user trust by demonstrating their commitment to operational security and risk management.
The Geopolitical Dimension: North Korea’s Role in Crypto Hacks 2024
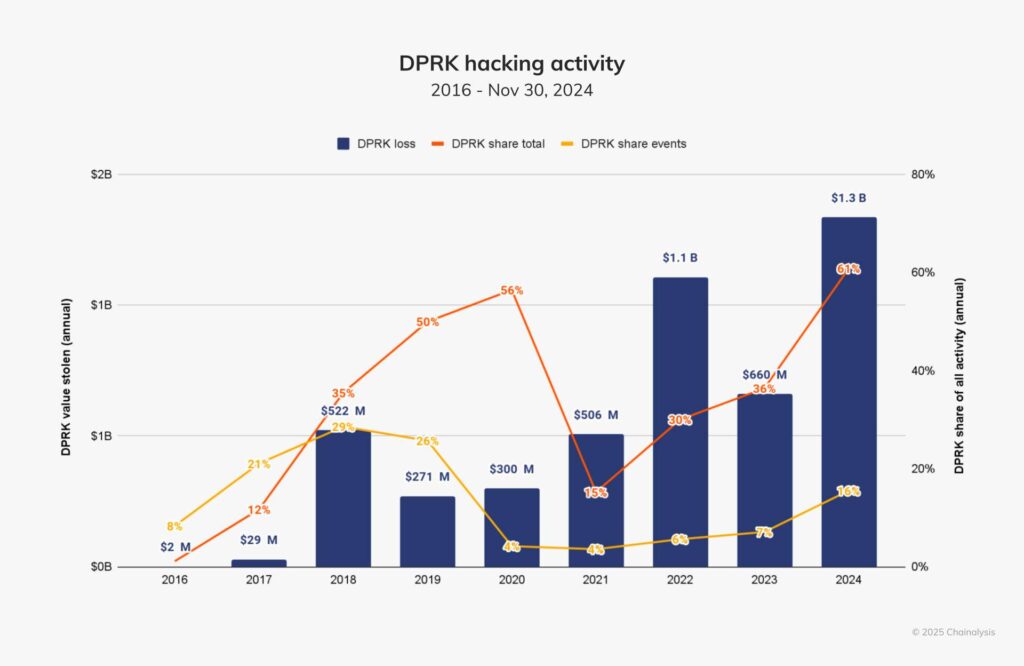
A staggering 61% of all stolen funds in 2024 were linked to North Korean-affiliated groups, including the notorious Lazarus Group. These state-backed actors are believed to have siphoned $1.34 billion across 47 attacks, a record-breaking haul. Analysts assert that these stolen funds are funneled into North Korea’s weapons development programs, circumventing international sanctions and raising significant geopolitical concerns.
The Lazarus Group’s activities included exploiting both DeFi vulnerabilities and centralized exchange weaknesses. Their operations highlight the intersection of cryptocurrency security and international security, with stolen digital assets becoming tools for geopolitical maneuvering. This dynamic underscores the need for global collaboration in addressing the threat posed by state-sponsored cybercrime.
International bodies, such as the United Nations and Interpol, have begun to take notice. In 2024, the UN Security Council’s report on cybersecurity flagged cryptocurrencies as a primary tool for sanction evasion, calling for a unified global response. However, enforcement remains challenging, as the decentralized and borderless nature of cryptocurrencies complicates traditional regulatory mechanisms.
Trends and Lessons from Crypto Hacks 2024
While December’s low losses suggest some progress in security measures, the annual trend reveals a troubling trajectory:
- Increased Complexity of Attacks: Cybercriminals employed more advanced techniques, including social engineering, sophisticated phishing campaigns, and supply chain attacks.
- Target Diversification: Beyond centralized exchanges, gaming platforms, and NFT marketplaces also faced heightened risks, with notable breaches like the $290 million PlayDapp hack.
- First-Half Surge: The first half of 2024 accounted for 84.4% of the year’s stolen funds, suggesting a seasonal or strategic pattern in cybercrime activities.
Moreover, the reliance on cross-chain bridges – critical infrastructure for interoperability between blockchains – emerged as a weak link. Several attacks exploited bridge vulnerabilities, leading to multi-million-dollar losses. This highlights the need for the industry to prioritize security in these critical components, which are essential for blockchain scalability and adoption.
Path Forward: Securing the Crypto Ecosystem Against Crypto Hacks 2024
Experts agree that addressing these challenges requires a multifaceted approach:
- Enhanced Security Protocols: Centralized and decentralized platforms must adopt advanced technologies like multi-signature wallets, real-time anomaly detection systems, and regular security audits.
- Regulatory Oversight: Governments and international bodies must establish stringent security standards and enforce compliance across the industry.
- User Education: Investors must learn to recognize phishing attempts, protect their private keys, and use hardware wallets for added security.
- Global Cooperation: Tackling the geopolitical dimension of cybercrime necessitates collaboration between nations, regulatory agencies, and blockchain organizations.
Additionally, cybersecurity experts advocate for proactive measures, such as bug bounty programs, to incentivize ethical hackers to identify vulnerabilities before malicious actors can exploit them. Companies must also invest in incident response plans to minimize damage and ensure a rapid recovery when breaches occur.
Future Prospects: Balancing Innovation and Security
The challenges posed by crypto hacks extend beyond financial losses. They threaten the credibility and trust essential for blockchain technology’s mainstream adoption. Innovations like zero-knowledge proofs and blockchain analytics tools offer promising avenues for enhancing security. These tools can help monitor transactions in real time, detect unusual patterns, and trace stolen assets across chains.
At the same time, the industry must balance innovation with robust security frameworks. Emerging trends, such as decentralized autonomous organizations (DAOs) and Web3 technologies, introduce new attack vectors that require proactive mitigation strategies. As the ecosystem evolves, stakeholders must adopt a holistic approach, integrating technological advancements with robust regulatory and security measures.
>>> Read more: Crypto Crime 2023 – Chainalysis Report
Conclusion: Learning from Crypto Hacks 2024
The record-breaking $2.2 billion in losses from crypto hacks in 2024 is a stark reminder of the vulnerabilities within the cryptocurrency ecosystem. The rise in centralized exchange breaches and the geopolitical implications of North Korean involvement underscores the urgent need for industry reform and global collaboration. While significant challenges remain, the industry has the tools and expertise to turn the tide. By prioritizing security, fostering international cooperation, and embracing innovative solutions, the crypto market can safeguard investor trust and ensure its resilience in an increasingly complex threat landscape.
Readers’ frequently asked questions
What makes centralized exchanges more vulnerable to hacks compared to decentralized platforms?
Centralized exchanges are particularly appealing targets for hackers because they act as custodians for large volumes of user funds. Unlike decentralized platforms, which allow users to control their private keys, centralized exchanges manage these keys on behalf of their users. If a hacker breaches the exchange’s security, they can potentially access all the funds stored there. Additionally, centralized exchanges often have complex operational systems and human involvement, which increases the risk of insider threats or social engineering attacks. The concentrated nature of assets and their management in centralized locations make them high-value targets for cybercriminals.
How does North Korea use the stolen cryptocurrency, and why are they so effective at hacking?
North Korean hacking groups, such as the Lazarus Group, use stolen cryptocurrency to fund state-sponsored programs, including weapons development. Cryptocurrencies offer an ideal medium for these activities because they operate outside traditional banking systems, making them difficult to track and confiscate. North Korean hackers are highly effective due to their extensive resources, advanced knowledge of blockchain vulnerabilities, and innovative techniques, such as exploiting cross-chain bridges or conducting spear-phishing campaigns. The stolen assets are often laundered through multiple transactions, mixing services, and exchanges to obfuscate their origin before being converted into fiat currency.
What steps can an individual investor take to protect their cryptocurrency from these kinds of hacks?
Individual investors can significantly reduce their risk by adopting best practices for crypto security. First, they should store their assets in hardware wallets or cold storage, which are not connected to the internet and thus less vulnerable to hacks. Second, investors should enable two-factor authentication (2FA) on all accounts and use strong, unique passwords. Third, it is vital to remain vigilant against phishing attempts, such as emails or messages that attempt to trick users into revealing sensitive information. Lastly, spreading funds across multiple platforms can minimize losses if one account or service is compromised. By taking these precautions, investors can protect their assets even in the face of increasing threats.
What Is In It For You? Action Items You Might Want to Consider
Reassess Where You Store Your Crypto
If you’re using a centralized exchange to store significant amounts of cryptocurrency, it might be time to rethink your strategy. Consider transferring a portion of your holdings to a hardware wallet or other forms of cold storage. By maintaining control over your private keys, you can significantly reduce your exposure to potential exchange breaches.
Stay Alert to New Threats
Cybercriminals are continually evolving their methods, and so should your defenses. Regularly educate yourself about the latest hacking techniques, such as phishing scams or vulnerabilities in cross-chain bridges. This knowledge can help you recognize and avoid potential traps that could jeopardize your assets.
Diversify Platforms for Risk Mitigation
Avoid placing all your assets on a single platform, even if you trust it. Spreading your holdings across multiple exchanges, wallets, or DeFi platforms can act as a safeguard, minimizing potential losses if one platform is targeted. This simple diversification strategy can add an extra layer of security to your crypto investments.










[…] >>> Read more: Crypto Hacks 2024: Lessons from $2.2 Billion in Losses […]