In the ever-evolving realm of cybersecurity, North Korea’s Lazarus Group stands out as a versatile threat actor, employing sophisticated tactics to execute cryptocurrency heists. This article delves into the intricacies of North Korea’s cyber operations, shedding light on their evolving strategies, the recent seizure of the crypto mixer Sinbad.io, and the alarming scale of their crypto thefts.
North Korea’s Strategic Shift to Cryptocurrency
Since 2017, North Korea has strategically shifted its focus from traditional financial institutions to the crypto sector. Faced with international sanctions, the regime found a lucrative means to fund its endeavors through cryptocurrency theft, particularly its nuclear arsenal and ballistic missile programs. The shift began with targeted attacks on South Korean entities during the 2017 cryptocurrency boom and gradually expanded globally.
Recorded Future’s Insight: A Glimpse into North Korea’s Crypto Heists
Recorded Future‘s recent report reveals the staggering extent of North Korea’s cryptocurrency theft, amassing a total of $3 billion since 2017. The regime, backed by highly trained computer science professionals, transitioned from targeting financial institutions to a broader strategy, encompassing individual users, venture capital firms, and alternative technologies. The illicitly acquired funds, crucial for circumventing international sanctions, undergo conventional laundering processes.
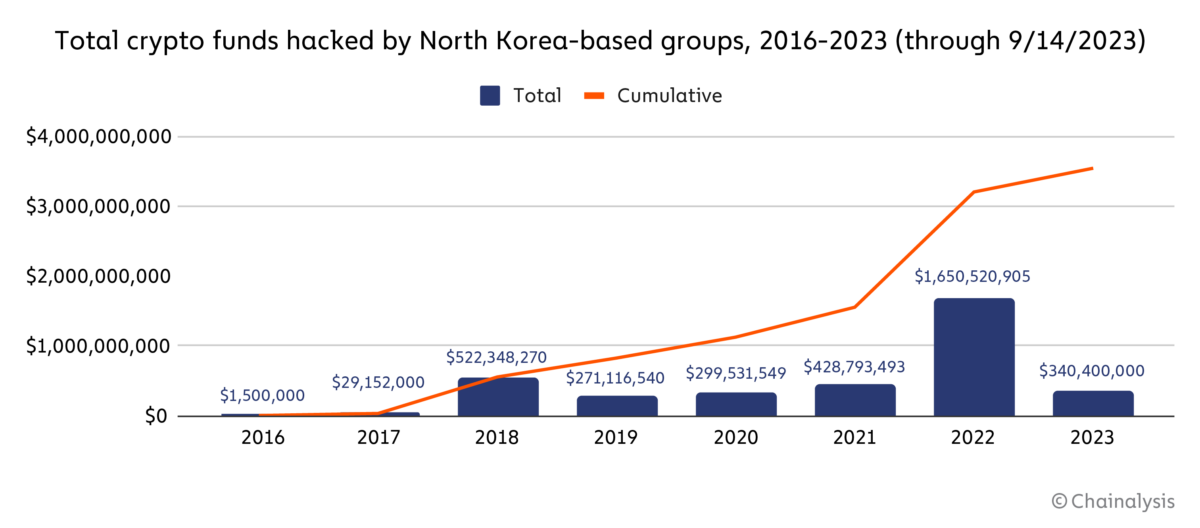
Chainalysis Data: Unveiling the Scale of North Korea’s Crypto Heists
According to Chainalysis, North Korea-backed hackers stole $1.7 billion in cryptocurrency in 2022 alone, marking a substantial portion of the global crypto losses that year. This surge in illicit gains reflects a fourfold increase compared to the country’s previous record. The report emphasizes the country’s desperate turn to crypto theft as a response to economic sanctions, contributing to 44% of the total stolen in 2022.
Crypto Mixer Seizures: Disrupting North Korea’s Money Laundering Efforts
In a significant move last week, the U.S. Treasury Department sanctioned and seized Sinbad.io, a virtual currency mixer integral to North Korea’s money laundering efforts. The mixer played a crucial role in obscuring the financial trail of ill-gotten proceeds from cybercriminal activities, including Lazarus Group’s involvement in high-profile heists like the Axie Infinity and Horizon Bridge incidents. The crackdown on Sinbad.io exemplifies global efforts to disrupt key components of North Korea’s cybercriminal infrastructure.
Lazarus Group’s Techniques: From Phishing to DeFi Hacks
North Korean threat actors, particularly Lazarus Group, employ diverse tactics ranging from phishing and supply chain attacks to infrastructure hacks. In 2022, they pilfered $1.7 billion, with 44% of the stolen cryptocurrency attributed to their operations. Notably, $1.1 billion was stolen through hacks of decentralized finance (DeFi) protocols, showcasing North Korea’s role in intensifying the DeFi hacking trend.
The Ongoing Threat: Decrypting the Cybernetic Cat-and-Mouse Game
Despite global efforts and sanctions, North Korea’s cybercriminal endeavors persist, fueled by the economic imperative to fund strategic programs. The recent collaboration among North Korean state-sponsored threat actors further complicates tracking efforts. As the crypto threat landscape evolves, collaborative defenses, stronger regulations, and enhanced cybersecurity measures become imperative to counter the persistent threat posed by North Korea’s adept cyber operations.
The cryptocurrency industry stands at the forefront of North Korea’s revenue-generating endeavors, prompting the need for heightened security measures, regulations, and investments. The ongoing cybernetic cat-and-mouse game necessitates a proactive stance from the global cybersecurity community to thwart North Korea’s relentless pursuit of crypto theft as a means to sustain its regime in the face of economic restrictions.











[…] Read more: How North Korea Steals Crypto […]
[…] >>> Read more: How North Korea Steals Crypto […]
[…] preliminary reports from cybersecurity firms and blockchain analytics companies point toward the North Korean state-sponsored hacking group Lazarus, well known for targeting cryptocurrency platforms to fund the regime’s activities. No […]
[…] SBI Holdings has played a central role in integrating digital assets into traditional finance in Japan. However, the loss may prompt regulators to reconsider the security standards of mining pools and custodians. For the broader industry, the incident reinforces Japan’s vulnerability in a region already targeted by North Korean hacking campaigns. […]