TL;DR
- Reporting and on-chain analysis have put custody arrangements for seized crypto under scrutiny after roughly $40 million in transfers exposed weaknesses in access controls.
- An on-chain investigation relied on blockchain transparency to surface the activity, underscoring ongoing risks in crypto custody for governments and institutional custodians.
Allegations that tens of millions of dollars in seized cryptocurrency were illegally accessed from government crypto wallets have placed renewed scrutiny on how seized digital assets are controlled after law enforcement actions. The case centers on the custody of seized crypto assets, not a failure of blockchain networks. Reporting and on-chain evidence have instead focused on access permissions and oversight within government-linked custody arrangements.
U.S. authorities have confirmed they are reviewing the claims. Public reporting has emphasized internal access controls rather than external hacking activity.
How the Alleged Movements From Government Crypto Wallets Were Detected
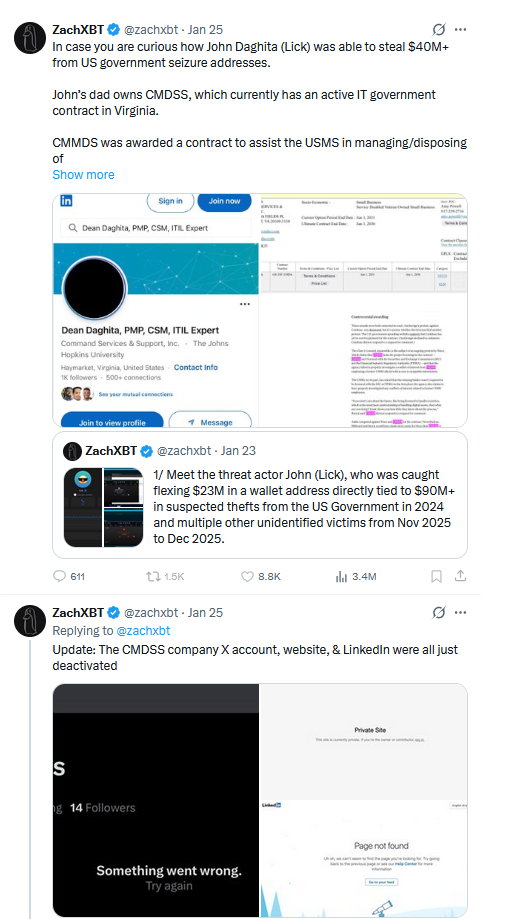
The allegations first surfaced through an on-chain investigation published by blockchain investigator ZachXBT. The analysis linked wallet activity to John “Lick” Daghita. He identified transfers traceable to addresses associated with seized assets managed under U.S. government authority.
According to the disclosures, a recorded Telegram dispute triggered the investigation. In that dispute, Daghita allegedly screen-shared wallet balances, showing more than $23 million in assets. Those wallets were later traced to addresses connected to long-standing U.S. seizure cases. This included funds seized from the 2016 Bitfinex hack. Because the transactions occurred on public blockchains, these movements from government crypto wallets were immediately visible once flagged.
Blockchain Transparency Versus Institutional Oversight
The episode illustrates the contrast between blockchain transparency and institutional monitoring. Public blockchains provide immutable transaction records that enable independent review. Custody oversight, however, operates off-chain through private keys, access permissions, and internal procedures.
In this case, blockchain records did not prevent the transfers. However, they did enable rapid external scrutiny. The incident has therefore raised questions about institutional crypto custody models that rely on trusted access rather than continuous external verification.
How Seized Crypto Assets Are Held and Controlled
After confiscation, authorities typically transfer seized crypto assets into wallets controlled by the U.S. government. Specialized custody contractors often provide operational support for the transactions. One such contractor, CMDSS, holds a 2024 contract with the U.S. Marshals Service. The contract covers management of certain categories of seized digital assets, including non-mainstream tokens.
These arrangements depend on defined access roles, internal audits, and key management policies. Reporting around this case has focused on crypto custody risk tied to how access privileges are assigned and monitored. The issue has not been framed as a technical exploit. Instead, the allegations point to insider access risk in the structure of seized crypto custody, as authorized users moved assets without immediate detection.
Scale of the Allegations and Asset Movements
ZachXBT’s analysis estimates that more than $40 million in seized cryptocurrency may be linked to the wallets in question. Some reporting references exposure to significantly higher transaction flows. One wallet identified in the disclosures reportedly held 12,540 ETH. That amount was valued at approximately $36 million at the time of analysis.
The investigation also highlighted activity in October 2024. During that period, roughly $20 million was moved. Most of those funds were later returned. Approximately $700,000 remains unaccounted for based on publicly available tracing. ZachXBT further disclosed that he received a small ETH transfer directly from one of the flagged wallets. This detail reinforced claims that the funds originated from seized sources.
Precise totals remain unconfirmed. Authorities have not released independent figures.
What Authorities Have Confirmed So Far
U.S. officials have stated that they are investigating claims of unauthorized access involving seized digital assets. The U.S. Marshals Service has confirmed that it is reviewing the allegations. It has not characterized the activity as a confirmed theft or protocol breach.
Public statements have remained limited. This reflects the sensitivity of digital asset seizure processes and the ongoing nature of the review. Authorities have emphasized that no conclusions have yet been reached.
Why Seized Crypto Custody Matters for Institutions
The implications extend beyond this case. The U.S. government controls substantial government-held bitcoin. Estimates place total holdings between roughly 198,000 and more than 300,000 BTC. Governments increasingly retain seized cryptocurrency rather than liquidating it immediately. As a result, custody controls become more critical.
Financial institutions relying on institutional crypto custody face similar challenges. Weaknesses in seized crypto custody can undermine confidence in broader custody models. This is particularly true where access controls and audit mechanisms lag behind the transparency of blockchain records.
Secondary Developments and Public Optics
Following the public exposure of the allegations, John Daghita launched a meme token known as $LICK on pump.fun. He retained a significant share of the supply. He also promoted the token through Telegram streams. These developments have drawn attention. They remain secondary to the core custody and oversight questions raised by the case.
>>> Read more: Bitfinex Hack: Lenient Sentencing Raises Questions
Conclusion
The allegations surrounding the $40 million seized crypto case have shifted focus toward custody of seized crypto and the internal controls governing access to government-managed digital assets. Blockchain transparency enabled early detection of the activity. Off-chain permission structures emerged as the point of concern. As investigations continue, the case highlights ongoing crypto custody risk in environments where asset visibility exceeds the robustness of institutional oversight.










